IT vulnerabilities are no longer exclusive to large tech companies or highly regulated sectors. Today, any organisation with a digital footprint is exposed to potential security breaches, often due to misconfigurations, outdated software, or uncontrolled access.
But what exactly does a vulnerability assessment involve? How is it carried out, what outcomes does it provide, and why is it increasingly essential to include it in any organisation’s security strategy?
In this article, we explain clearly and directly what this type of assessment entails, what to consider before choosing a provider, and how it can help you anticipate problems before they escalate into serious incidents.
What is a vulnerability assessment?
A vulnerability is a weakness in a system, application, or configuration that could be exploited by an attacker to compromise an organisation’s security. If left undetected, these vulnerabilities can become entry points for incidents that disrupt operations, expose sensitive data, or lead to non-compliance with regulations.
Vulnerability assessment is a proactive practice used to identify, assess, and classify these weaknesses before they cause real problems. Using a combination of scanning tools and systematic review, the process offers a clear overview of system security and helps guide informed decisions on corrective actions.
For businesses, this kind of assessment is especially important because it allows you to:
- Prevent cyberattacks proactively
- Detect misconfigurations or outdated software
- Prepare infrastructure for audits and compliance reviews
- Reduce risk without disrupting critical services
In short, it’s an essential tool to strengthen your security posture and improve digital resilience.
What does this type of assessment involve?
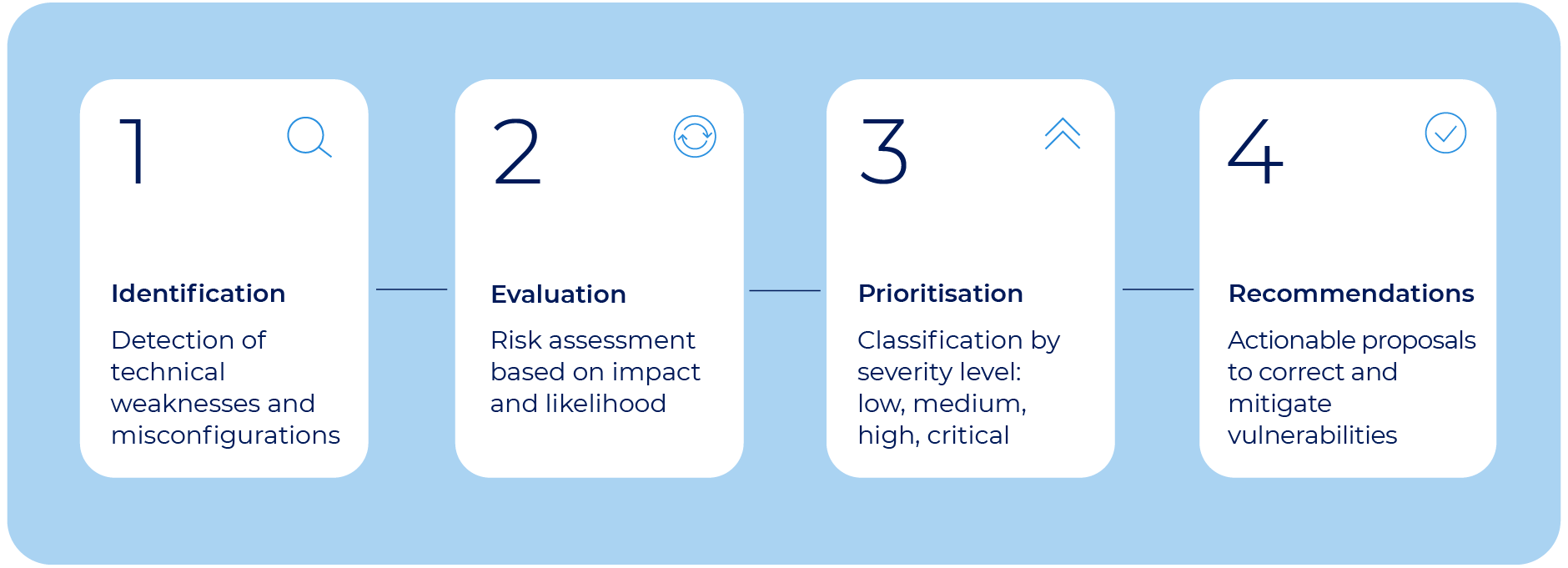
A vulnerability assessment is more than just running a scan for errors. It’s a structured process that allows a deep understanding of the security risks facing a technology infrastructure. While specifics may vary depending on the environment and provider, the process typically involves four key phases:
1. Vulnerability identification
A technical assessment is conducted to detect weaknesses in operating systems, applications, exposed services, or network configurations. This includes both known threats (from public vulnerability databases) and custom configurations that might go unnoticed.
2. Risk evaluation
Each finding is assessed in context. Not all vulnerabilities have the same impact or likelihood of exploitation. This phase evaluates technical severity as well as the system’s criticality, level of exposure, and dependencies.
3. Action prioritisation
Vulnerabilities are classified by risk level—low, medium, high, or critical—so that organisations can focus on addressing the most urgent threats first.
4. Recommendations and remediation
Finally, the assessment includes actionable recommendations to mitigate identified risks. These might range from updating software or closing ports to thoroughly reviewing service configurations. In many cases, exportable reports are delivered to support internal documentation or audit requirements.
This process allows organisations not just to identify their weak points but to define a realistic, actionable plan to improve security without interrupting day-to-day operations.
Types of vulnerability assessments in business environments
Different organisations face different levels of exposure and have varied infrastructure setups. For that reason, vulnerability assessment can and should be tailored. Broadly speaking, two main approaches are common:
Full system assessment
A comprehensive review of the system, including open ports, running services, internal configurations, and installed applications. Ideal for major updates, server onboarding, or preparation for compliance audits.
Customised assessment
This option focuses on specific goals, such as reviewing a single service, a limited port range, or a mission-critical server. The scope and parameters are adapted to the business context.
These approaches can be used separately or combined. For instance, a full assessment may be scheduled periodically, while a customised one might be triggered by specific infrastructure changes or audit requirements.
What matters most is viewing the assessment not as a one-off task, but as part of a continuous security lifecycle.
What should a good vulnerability assessment deliver?
Vulnerability assessment isn’t just a technical exercise—its true value lies in the quality and clarity of the output. A good assessment should result in a detailed, clear, and actionable report that helps technical teams and security leaders make informed decisions.
Here’s what to expect from a reliable assessment:
1. Summary of findings
An overview of the system’s security status, listing all vulnerabilities found, categorised by severity:
- Low: minimal impact but worth addressing
- Medium: could impact services in specific situations
- High: significant threats requiring priority attention
- Critical: severe risks that could compromise the infrastructure
2. Risk classification and prioritisation
Each vulnerability should include a risk assessment based on impact, likelihood, and context (e.g. affected system, level of exposure, operational role).
3. Mitigation recommendations
A meaningful assessment goes beyond listing issues—it provides specific, practical solutions. These can include technical fixes (updates, config changes, closing ports) and recommended security practices tailored to your environment.
4. Exportable and audit-ready reports
Documentation should be shareable and audit-compliant, typically delivered in multiple formats (PDF, CSV, HTML) to support internal reporting or external certification processes.
In essence, the assessment should not stop at diagnosis—it should enable action.

Why is vulnerability assessment especially relevant for businesses?
In business environments, cybersecurity directly affects business continuity, customer trust, and compliance. That’s why regular vulnerability assessment is a fundamental part of a solid security strategy.
Here’s why it matters:
1. Prevent attacks before they happen
Many major security breaches stem from known, preventable vulnerabilities. Assessment helps detect them early and reduce your attack surface.
2. Minimise operational and reputational impact
Security incidents can disrupt services, lead to data loss, and damage brand reputation. Anticipating these issues helps avoid costly last-minute responses.
3. Support regulatory compliance
Standards like ISO 27001, PCI DSS, or ENS require organisations to proactively identify and manage vulnerabilities. A documented assessment helps demonstrate this commitment.
4. Enable better decision-making
Clarity on system risks helps prioritise investments, plan updates, and define stronger internal protocols—aligning IT decisions with overall business goals.
In short, vulnerability assessment strengthens digital resilience and enhances a company’s ability to respond to emerging risks.
How often should you conduct one?
There’s no one-size-fits-all frequency. It depends on your infrastructure, the criticality of your systems, and how often they change. That said, several moments make a vulnerability assessment especially valuable:
After infrastructure changes
Server onboarding, system migrations, or configuration updates can all introduce unexpected weaknesses. An assessment right after ensures nothing was left unprotected.
Before compliance audits
If you’re preparing for an audit—internal, client-driven, or for certification—a prior assessment helps you catch and resolve issues ahead of time.
Periodically as a preventive measure
Even in stable environments, scheduling an assessment quarterly or semiannually helps identify new threats or unnoticed changes.
In response to alerts or incidents
Unusual activity, unauthorised access attempts, or unexplained system behaviours may signal a security issue. An assessment helps assess the situation and reinforce defences.
Embedding this into your regular IT operations helps manage risk proactively, without disrupting daily work.
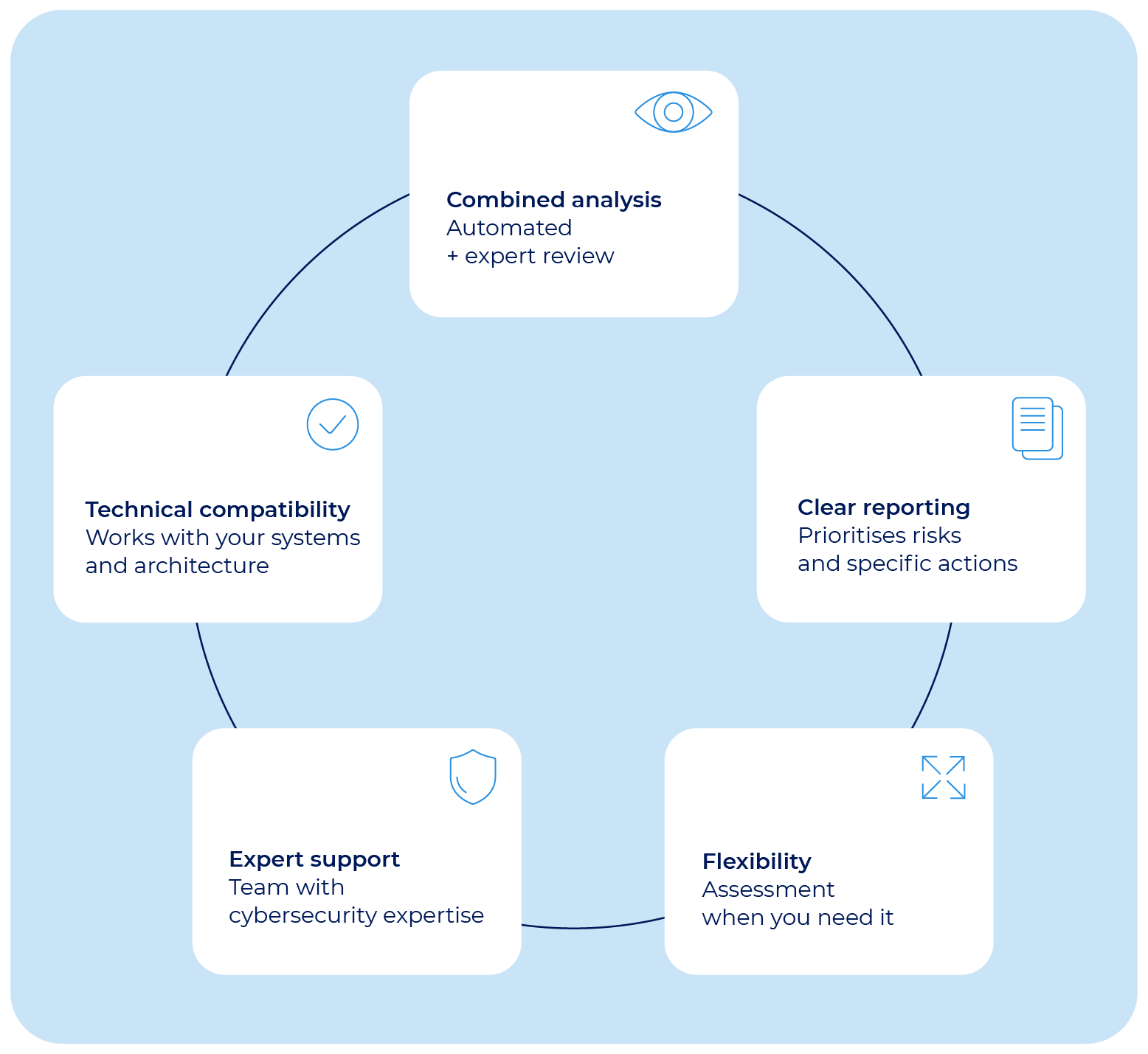
What to consider before choosing a vulnerability assessment provider
Choosing a vulnerability assessment provider is a strategic decision. Not all services offer the same scope, depth, or reliability. Here’s what to look for:
Does it include manual assessment, or just automated scans?
Automated scans catch common threats, but complex environments often require deeper manual review to uncover misconfigurations or subtle issues.
Is it compatible with your tech environment?
Ensure it works with your OS, architecture, and applications. Customisation should be possible based on your infrastructure and security priorities.
What kind of reporting is provided?
The output should be clear, prioritised, and actionable. Exportable formats (PDF, CSV, HTML) are useful for sharing internally or with auditors.
Can it be run on demand?
Flexibility to run the assessment whenever needed—rather than on a fixed schedule—is key to adapting to infrastructure changes.
Is expert support included?
Having access to a team that understands both cybersecurity and your environment makes a big difference when interpreting results and implementing fixes.
Taking the time to assess these criteria helps ensure the assessment becomes a practical, strategic tool—not just a technical exercise.
When infrastructure and security are designed together
Vulnerability assessment is often seen as a one-off exercise or a checkbox before an audit. But in critical environments, security shouldn’t be separate from infrastructure—it should be part of its design.
Planning, hosting, and operating infrastructure with security in mind from the start reduces risks, anticipates problems, and enables faster response when needed.
That’s why working with a provider who not only offers compute and storage capacity but also integrated security services—like vulnerability assessment—can be a strategic advantage. It allows for better coordination between infrastructure management and protection measures.
At Adam, this type of assessment is built into our IaaS platform. Our team’s familiarity with the environment enables us to deliver more accurate diagnostics, respond quickly with corrective actions, and support our clients in both prevention and incident response.
This article has been written by
Adam